INTERNET
Firewall, VPN and Wireless Access
We can design and implement a secure network to the internet while providing you ways to connect to your office or connect your office to another office.We provide secure Wireless Access solutions which give you freedom to work from anyware to anywhere.
Domain Management, Reclamation & Protection
Is your web content being "held hostage" by a former developer, or have you lost control of your content by letting your hosting lapse? We can retake control of a lost domain / web addresses and restore your content to ensure website persistence through proper management.
CLICK HERE TO TAKE BACK CONTROL
Protect Your Domain Name from Being Stolen!
Getting your domain name stolen is one of the most devastating things that can happen to you on the internet. In an economy where online presence is a critical part of a successful business strategy, losing control over a domain name is a frightening thought. In an instant, your website, company email, client addresses, and even other accounts connected to them can wind up under the control of saboteurs. There are laws protecting your ownership, but court procedures are time consuming and expensive, and by the time you get your domain name back, your business reputation may be irreparably damaged.
CLICK HERE TO PROTECT YOUR ONLINE ASSETS

Professional Voice and Data Cabling
Professional Voice and Data Cabling involves designing, installing, and maintaining cabling systems that support a range of communications infrastructure including phone services, data transmission, and LAN connectivity. Our certified professionals ensure optimal performance, system scalability, neat & logical deployment, and seamless integration with existing networks.
Internet Connectivity
NEED A TECH GUY will work with you to select the most appropriate internet service provider for the best price and without any extra unneeded costs. Since wiring and infrastructure issues often lead to general increased latency and illusive, intermittent connection issues, we will identify and repair any deficiencies ensuring that you get the most reliable internet and network connectivity.
Phone Connectivity
NEED A TECH GUY is proudly partnered with Vonage Business (Formally Vocalocity), RingCentral and Nextiva. IP Phone Systems go beyond small business phone service. Powerful features deliver value by giving you the right balance of flexibility and control, so you can work smarter every day.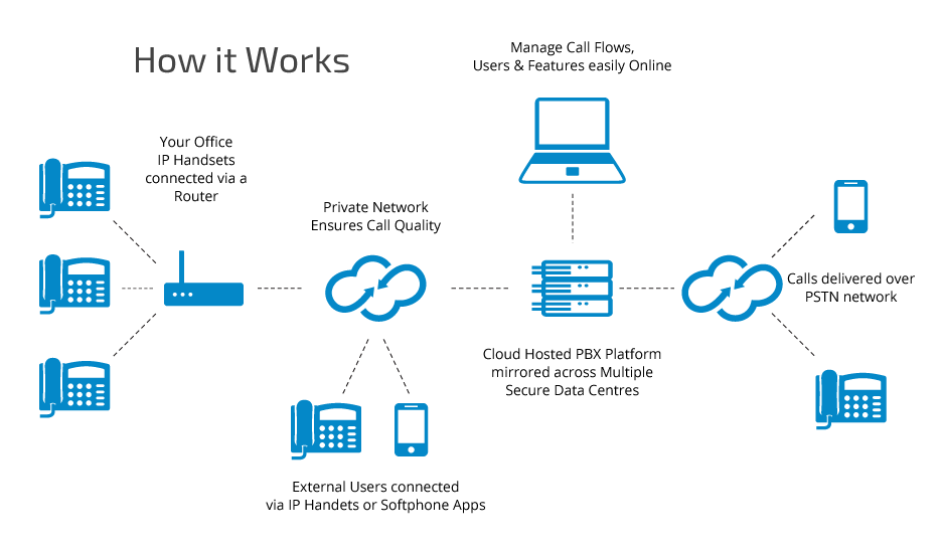
24/7 Call Answering Services
A 24/7 call answering service is an answering service staffed by friendly, professional customer experience experts who can answer your customer calls day or night. Excellent for after-hours calls or daytime overflow calls, a 24/7 answering service ensures your customers always reach a live person and receive superior customer care no matter when they call your business.
CLICK HERE TO LEARN MORE ABOUT CALL ANSWERING SERVICE
Dark Web Scanning
The Dark Web is home to vast amounts of ill-gotten data not readily accessible to the average Internet user. NEED A TECH GUY can search the dark web for you, combing through its large databases of stolen usernames, passwords, Social Security numbers, and credit card numbers for sale to ensure your personal information is not compromised.
Office 365 - Stay connected wherever you are
- Always up-to-date, wherever you access it: Office 365 syncs emails, calendars, and contact information across your devices in real time, so everything is up to date no matter which device is in your hand.
- Scheduling made simple: Shared calendars let you see when people are free or busy at any time, making scheduling easy and hassle-free, no matter where you are.
- Safeguard your mobile data:If you lose your phone, don't panic! With Office 365 you can wipe your phone's data remotely to prevent unauthorized access to your information.
Exchange |
OneDrive |
SharePoint |
Microsoft Teams |
Email and calendars |
Instant messaging and online meetings |
||
1 TB of secure cloud storage per user |
Intranet and team sites |
||
Office apps on the web |

What is phishing? Whereas SPAM is simply unwanted and unsolicited, phishing emails are expressly designed by a malignant actor to harm a company or individual by fooling the recipient into providing sensitive information. Phishing emails often take the form of a legitimate-looking message from a trusted sender.